Types of Tunneling
The type of VPN used by an enterprise determines the tunneling method used in a VPN. A VPN connection can either be a Site-to-Site VPN connection established between two networks or a Remote Access VPN connection established between a remote client and a VPN server at the corporate intranet. The two types of tunneling methods that correspond to these VPN connections are as follows:
- End-to-End tunneling: Connects a remote user’s personal computer and the VPN server, which acts as a gateway between the Internet and the corporate LAN of an enterprise. It is used in a Remote Access VPN connection. Tunneling procedures, such as data encapsulation and decapsulation, are carried out at the endpoints of the tunnel. The VPN client software encapsulates the data packets before sending it across the tunnel to a VPN server. The VPN server decapsulates the data before forwarding it to the corporate LAN.
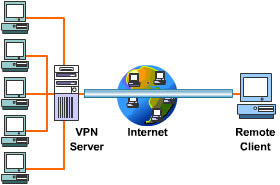
- Node-to-Node tunneling: Connects the gateway devices that are situated at the edge of two private networks. It is used in a Site-to-Site VPN connection. A gateway device can be a router, a firewall, or some similar device that acts as a VPN server. In this setup, a VPN client is a remote user situated on the LAN of an enterprise. The tunnel extends from one gateway device to another and does not extend to the remote user’s computer. The gateway device at the edge of a LAN encapsulates the data received from a computer within the LAN and performs encapsulation before sending it across the tunnel. The gateway device at the other end of the tunnel decapsulates the data before forwarding it to the LAN.

Layer 2 and Layer 3 Tunneling
Tunneling methods are differentiated based upon the type of tunneling protocol used to encapsulate data. Layer 2 and Layer 3 tunneling involve the use of tunneling protocols that correspond to the data link layer and the network layer in the Open System Interconnection (OSI) model.
Layer 2 tunneling protocols, such as PPTP and L2TP, use frames to encapsulate data payloads. PPP is generally used as the carrier protocol in an IP-based internetwork, such as the Internet. These protocols use frames to exchange data across the tunnel endpoints. Before transmission, a PPP frame is attached to the data payload. This payload is encapsulated using the GRE protocol. Tunnel maintenance and control messages are used to create, manage, and terminate a tunnel. Layer 2 tunneling is predominantly used in a Remote Access VPN to create point-to-point tunnels between a remote client and a VPN server.
Layer 3 tunneling uses network layer tunneling protocols, such as IPSec in the tunnel mode and IP over IP, for the exchange of data packets. These protocols use packets as a medium of exchange. Layer 3 tunneling involves the addition of a new IP header to an IP packet before sending them across a tunnel created over an IP-based network. Note that the use of Layer 3 tunneling protocols is confined to IP-based networks. This type of tunneling is used in a Site-to-Site VPN to connect two or more private networks. However, Layer 3 tunneling protocols can also be used in a Remote Access VPN. Mutual authentication is generally not carried at the time of establishing a tunnel.
| Note |
To create a tunnel, both the devices at the endpoints of a tunnel must support the tunneling protocol. For example, in a Remote Access VPN, both the VPN server and the VPN client must be configured to implement the same tunneling protocol. |
|
Feature |
Layer 2 Tunneling |
Layer 3 Tunneling |
|---|---|---|
|
Protocol support |
Provides support for various network protocols, such as IPX and NetBEUI. |
Provides support for only IP-based networks. |
|
Authentication |
Supports user-based authentication using authentication protocols. Hardware-based authentication mechanisms, such as tokens and smart cards, are supported using EAP. |
Supports device-based authentication methods, such as digital certificates. |
|
Assignment of IP addresses |
Supports dynamic assignment of IP addresses to VPN clients by the VPN server at the time of connection establishment. |
Assumes that IP addresses are assigned prior to the creation of a tunnel. |
|
Encryption |
Supports encryption mechanisms, such as Microsoft Point-to-Point Encryption (MPPE), and cryptographic algorithms, such as DES. |
Supports similar encryption mechanisms as Layer 2 tunneling protocols. In addition, IPSec consists of a protocol suite that provides strong encryption. |
The tunneling feature combines with the various data encryption mechanisms used in a VPN to ensure a high level of security.