Computer Viruses.
![]() What
are computer viruses?
What
are computer viruses?
Fred Cohen's well-known definition is "a computer virus is a computer
program that can infect other computer programs by modifying them in such a way
as to include a (possibly evolved) copy of itself". Several other
definitions of "virus" have been proposed:
1. A computer virus is a self-replicating program containing code that
explicitly copies itself and that can "infect" other programs by modifying them
or their environment such that a call to an infected program implies a call to a
possibly evolved copy of the virus.
2. A virus is a self-replicating piece of code that attaches itself to other programs and usually requires human interaction to propagate.
Classification of computer viruses (we are purposely ignoring macro viruses for now)
· Boot or file (executable) infector
· Memory-Resident or nonresident
· Appending/prepending or overwriting or companion


Pure boot sector viruses can only spread if you boot from an infected floppy diskette. You can retrieve and save files all day long to an infected diskette, but as long as you didn't boot with it, you're safe. In the past, to eliminate the biggest threat of computer viruses all you had to do was not boot from a diskette. Boot sector viruses replace a PC's normal boot code and take control during the initial stages of the PC's start sequence, although there are several different places where it can insert itself in the process.
The very first IBM PC virus, Brain, was a boot virus. Stoned, Michelangelo, AntiEXE, Ping-Pong, and Monkey are all familiar names of boot viruses.

Many viruses, including the original Brain boot virus, add extra code to pass along the original boot sector to any disk inspection tools looking for the boot sector. This way, they have a better chance of hiding (stealth). However, anyone looking with the right tools without the virus in memory (i.e., booting from a known, clean, write-protected DOS diskette) will see the new bogus boot sector.
On every PC, many processes and checks must be made prior to any program or user being able to execute the first command. Much of the initial boot sequence, as shown below, is dedicated to performing simple hardware self-checks and is the same regardless of the operating system. Once the operating system (OS) begins to boot, the sequence differs according to the particular needs of the OS.

After you flip the power switch, the power supply does a quick self-check and sends a signal to the CPU to start.
The CPU initializes itself and starts executing hardware self-check code located in the read-only memory basic input/output system ( ROM BIOS) chip located on the motherboard. The ROM BIOS chip contains instructions that are "burned into" the chip and aren't normally changed to remember hardware and configuration settings and the instructions to find and start the operating system boot process.
A test of system random access memory (RAM) and a further set of ROM self-checks, often referred to as the power on self-test (POST) is performed. Any errors found will usually result in audible error beeps, and be displayed if possible.
The system then searches for the first boot drive is checked and the master boot record (MBR) and partition table. The MBR tells the CPU which partition and in what sector to continue the boot process from.
The MBR then tells the PC where to locate the primary boot sector of the default operating system. This process is identical for every PC regardless of the operating system. Thus, a boot virus located on a booted floppy will be able to successfully infect the boot area of all hard drives. When an infected PC boots, the infected boot sector is given control. During this stage of the booting process, the virus can execute its payload damage regardless of the operating system
A nonmemory resident (also known as nonresident) virus executes, does its business, and then exits. It doesn't activate again until the next infected host file is started. On the other hand, memory-resident viruses use host files as a launching point and reside in memory long after the original host file has exited. A memory-resident virus will hook itself into the interrupt subroutines. Then whenever a user or program requests a particular service, the virus has first choice on what it wants to do. For instance, most boot viruses will stay in memory and infect any floppy disk that is accessed for any reason.
· COM file

Many executables contain lots of free space, especially large .EXEs. The free space is usually reserved for a data buffer area to store temporary data. Cavity viruses look for program files with large amounts of free space, and if large enough, store themselves there. This overwrites part of the host file, but without increasing the size or harming functionality. When the host file executes, the virus runs and does what it was coded to do. The borrowed buffer area is often overwritten with temporary data, as was intended by the host file, erasing the virus code. By then the virus is in memory or already in a new host.

Multipartite
viruses use more than one avenue of infection. The typical
multipartite virus infects .COMs, .EXEs, floppy disk boot sectors,
and hard drive MBRs. When you boot with a floppy diskette containing a
multipartite virus, often it will infect your hard drive's boot sector and start
to infect executable files. Because they contain subroutines to infect in more
than one way, their code is often large.
Virus Propagation Mechanisms
Removable Storage
E-mail and Downloads
Shared Directories
Defending Against Viruses
Antivirus Software – Virus Signatures, Heuristics, Integrity Verification
Configuration Hardening
User Education
The typical life cycle of a computer virus is something like this:
1. A virus gets created and released.
2. The virus infects a few PCs and gets sent to an antivirus company.
3. The antivirus company records a signature from the virus.
4. The company includes the new signature in its database.
5. Its scanner now detects the virus, and the threat of the virus is lessened.
If you're a virus writer, your creation can't spread all over the world if it's being detected and cleaned within a few weeks of its release.
Virus writers started fighting back with more sophisticated virus defense mechanisms to go undetected longer. Thus, the war of the virus writers against the antivirus vendors began. In a sense, the antivirus industry created more, faster, and smarter viruses. Some virus defenses include polymorphism and stealth
Virus writers saw that the best way to stop or slow down antivirus scanners was to make sure there was no constant string of bytes that could become an antivirus signature. For our purposes, encryption is the process of a virus rearranging its code so that it no longer looks like its former self in order to defeat antivirus scanners (see Figure below) The virus executes, decrypts itself, does its thing, then rescrambles its bytes before saving itself back to the disk. Virus authors on the forefront of technology started to research and utilize professional encryption techniques. In order to be able to use encryption, a virus must be able to decrypt the encrypted code (called decryption) and encrypt itself "on the fly."
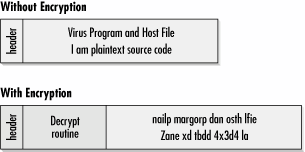
How could a virus scanner locate a good signature? The solution involved searching for the decryption routine (sometimes called a decryptor) that had to be located at the start of every encrypted virus. The decryption engine became the signature. Decryption routines can't be scrambled because they must remain as plain code to execute and start the unscrambling process. To fight back, virus writers started writing smaller and smaller decryption processes. Smaller decryption signatures increase the chance that an antivirus scanner will produce a false-positive. Still, even with ever-smaller decryption processes, most antivirus companies were able to detect encrypted viruses reliably.
Although most viruses use encryption to hide, other viruses use encryption as a means to make the removal process more difficult for antivirus programs. They encrypt the boot area or files when they first infect. After infection, they decipher the encoded host file or boot sector when it is needed. If you remove the virus or boot with a clean diskette, the file or boot area remains encrypted and inaccessible.
Polymorphism is virus encryption done better. Some bright virus writers decided that the only way to defeat antivirus companies was by randomly changing the encryption/decryption portion of the virus. Each time the virus starts, it might change the random number generation routine used, the length of the number used (called the key), the number of bytes encrypted, and the place the encryption subroutine is located in every file. This is called polymorphism. How can antivirus scanners find a signature when everything, including the encrypting subroutine, randomly changed? Potentially, there are billions of combinations that scanners would have to try against each host file. Click here for the example of the 1st polymorphic virus.
The first polymorphic engine, Dark Avenger's Mutation Engine(MtE or DAME), was released in 1991. MtE allowed the static, unchanging bytes of a virus to be less than a handful. With a static signature so small, the risk of false positives by antivirus scanners suddenly became unacceptably high. MtE and the other polymorphic engines that followed were highly successful at keeping antivirus companies at the workbench. Polymorphic engines were one of the first malicious implementations to seriously challenge the professional debugging teams of the antivirus industry.
It turns out that although polymorphic encrypting viruses were different looking each time, there is no true randomness in the computer world, and a reliable signature can be calculated even in random-looking code. It just takes more digging. Some antivirus products included signatures for each resulting infected file copy. But since one virus could create billions of different copies, this method was quickly rejected by most companies as a workable solution. Researchers started getting a quicker detection rate by learning how the encryption engines worked and decoding each scanned file by reverse-engineering the encryption engine's steps. This took time and meant that scanning engines would potentially have to check each file against a large number of encryption routines.
The most successful scanners use an emulation engine that temporarily load scanned files into a protected area in RAM that simulates the computers operational environment. The virus thinks it is running, even though it is unable to access any part of the computer outside the emulated area, and decrypts itself. The decoded virus code is scanned by the antivirus program. Best of all, it only takes one signature to recognize the billions of different copies of the same virus. Today, there are dozens of polymorphic encryption engines available to virus writers, but good scanners can detect all their variants. When a new engine comes out, it's only a matter of a few hours of work on the antivirus researcher's PC, thereby deflating the potentially damaging encryption routine that took the virus writer weeks or months to write.
Metamorphic viruses change the functionality of a virus as it spreads. Metamorphic viruses don't have a decryptor or a constant virus body, but are able to create new generations that look different. The W32/Apparition virus was the first-known 32-bit virus that didn't use polymorphic decryptors to evolve itself in new generations. Rather, the virus carries its source and drops it whenever it can find a compiler installed on the machine. The virus inserts and removes junk code to its source and recompiles itself. In this way, a new generation of the virus will look completely different from previous ones. This technique is even more dangerous on platforms such as Linux, where C compilers are commonly installed with the standard system, even if the system is not used for development.
Viruses that contain special coding to elude antivirus researchers and tools are considered stealth viruses. The first PC virus, Brain, included stealth code, and redirected requests to view the infected boot sector to the original boot sector code now placed at the end of the diskette. Stealth viruses can use hundreds of different routines to hide from prying eyes. One of the most common routines is for a virus to remove itself from a file when a virus scanner is being run. Stealth is one more reason you should always boot from a clean, write-protected boot diskette prior to running a DOS virus scan.
If the virus is in memory, it can hide. Viruses often hide increases in infected file size by modifying what DOS returns to the user. It does this by monitoring the DOS interrupts that return memory and file information. For example, if a user types in the DIR command while the virus is in memory, the virus code will pass along the request to DOS. DOS collects the requested information and tries to return it to the user. The virus steps in and does the necessary calculations so that the telltale signs of its infection are hidden.
Stealth technologies for the DOS operating system were reborn as rootkit technologies for the Windows operating system 10 years later. Malicious programs for the Windows operating system started using stealthing technologies to hide their presence in the system in the first years of the new millennium. In early 2004, Kaspersky Lab encountered a surprising program that couldn't be seen in the Windows processes and files list. For many antivirus experts, this was a new beginning – understanding stealthing technologies for malicious programs for Windows – and it was the harbinger of a major new trend in the virus writing industry.
The term “rootkit” stems from Unix utilities that are designed to provide a user with unsanctioned root access within the system without being noticed by the system administrator. Today, the word rootkit covers dedicated utilities used to conceal information in the system, as well as malicious programs with functionality which enables them to mask their presence. These include the manifestations of any third-party registered applications: a string in the list of processes, a file on disk, a registry key or even network traffic.